Here are 50 concept sketches of the possible outcomes of the multiple online identity management project. They were finished in one-day’s brainstorm and the purpose of this exercise is to explore broader possibilities and encourage more innovative elements in this project.
Monthly Archives: May 2013
Tutorial notes – 29-30/05/13
On May 29th & 30th, I had two tutorials with module tutor and project adviser and the following is the note of main discussion topics:
- For the multiple online identity management project, the next step research needs to make clear the concept of core identity vs. dynamic identity of human beings and the both benefit and disadvantage aspects of multiple identities;
- Discussion of the potential outcomes: story telling with video+ interactive mock-up interface
- Co-design workshop: purpose, people to contact with, physical materials should be involved to encourage engagement;
- Stakeholders interview + interactive exercise (online identity mapping);
- Tutorial plan;
- 50 concept sketches discussion.
In summary, the next step research will go deep in the direction determined by the project’s first stage research, which includes deeper case study (combined with customer interviews), literature reading (from specialist’s recommendation), understand of user behavior in detail, stakeholder research with interactive exercises, iterative tests and feedback and stakeholder networking:
3 main password management services
(Elements comparison table of three main password management services)
There are three main password management services nowadays-1Password, LastPass and KeePass– and their system and function is quite similar to the outcome my Master Project would like to achieve. Therefore it’s very meaningful to study on these three services. As a start I gave a trail with each of them and experienced how they work. Then I collected more online comments and tutorials from others to make a comparison within these three services. As the above table shows there are many different features within the password management services and here are the common elements:
- Master password: To get access to the management system, users need to set a master password and must remember it-the service cannot help you get back the master password any longer because it will not save the password to guarantee users’ security control;
- Password separation: As users get access to the password management service with one master password, there is no need for them to remember password for each online platform. Therefore users can set super strong passwords for each site and the service could help users generate random and strong passwords- it encourages users to set stronger but harder remember passwords;
- Browser plug-in: Most services are based on browser and work as plug-in. In this way when users login or create a new account the plug-in could help automatically generate, remember and fill in accounts information and that saves users’ lots of time;
- Devices sync: Most services support data sync across various devices and systems. It works as cloud storage or data file saved on Dropbox. However, the user experience across devices might be affected by inconsistent interfaces, prices or developers;
- Function: Most services are focusing more on password management. Some of them offer identity or account management as well but just work in the same approach of password management and that don’t fit IDM requirements quite well.
Mobile consumers want privacy- report summary from MEF
Andrew Bud, global chairman of MEF, posted an article on VentureBeat to discuss the survey report of mobile consumer attitudes towards app privacy by MEF (global community for mobile content & commerce).
This survey was far reaching with over 9,500 respondents across ten countries. In the report summary, it analyzes privacy in the context of four component parts:
- Transparency: Consumers understand the impact of mobile apps on their privacy and want app providers to explain what and how their data is collected and used;
- Comfort:Only a third (37%) of consumers are comfortable sharing personal information with an app;
- Security: Most mobile users trust app providers to protect their personal information;
- Control: A third of consumers think they have complete control over how their personal information is used for advertising purposes. However, in reality it is unlikely consumers are able to control the way companies use their personal information.
These statistics are very useful evidences that users need make sense and have control of their personal data exchanged with online platforms. And the report mentions that in reality consumers need to face the limitation of privacy control. Therefore, this project needs to explore what the new service can do to help users gain more control under the limited situation.
User behavior change on Facebook with time
VentureBeat posted an article about Facebook usage data collected and analyzed by Wolfram Alpha (Facebook Personal Analytics) last week. It’s interesting to find that user life pattern actually changes with time in this case.
For example, friends on Facebook vary with time. The result from Wolfram Alpha says “When you’re younger, most of your friends are your own age, but the range of ages broadens as you get older.”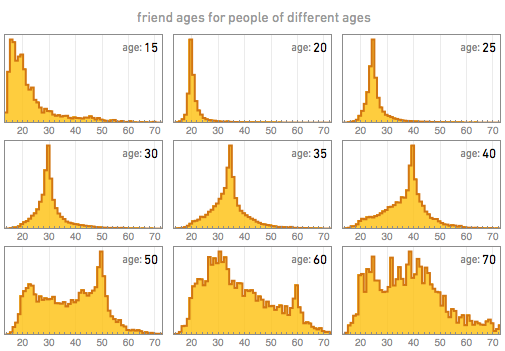
And people talk different things as they getting older (the two colors represent gender):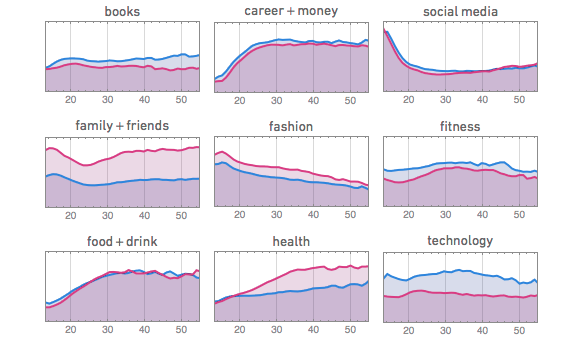
Though the report says the data is limited to the small number Facebook users who let Wolfram Alpha use it, it’s very meaningful statistic and evidence of user’s changing needs of online platforms with time- because the online audience and behaviors change, what they want to express and show who they are may vary as well.
Idea of ID token-13.05.16
In the book Hidden in Plain Sight, Jan Chipchase said “the most common carried objects around the world” is “keys, money and mobile phone“. Therefore I come up the ideas that the token for IDM could be with the keys or mobile phones because other kinds of wearables may cause users stressful to remember to take with every time.
Personal- Privacy by design
Personal is a well-designed and quite close case for my project. It’s a service which helps people manage and share personal information. Personal works within the concept of “Privacy by Design”, which may be very helpful for my project.
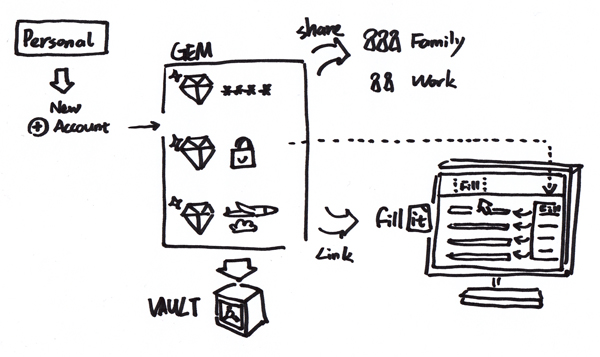
The following sketch shows how Personal works:
All personal information is saved in Gems, grouped within function and feature categories, and all Gems are collected in data Vault, which provides high security level. Users could choose data to share with others such as family members and work peers. In addition, the data on Personal could be linked to its another product Fill It, which is embedded as a bookmark of browser and helps users fill in online forms and log in automatically with the information kept in Personal account.
The story in Fill It’s video mentions users’ multiple identities online and at the end of the story, it says the benefit of the service is to “Let users to get back to the important things in life” – that supports my project topic a lot.
Concept for the project result
Based on previous ideas from secondary research and participants communication, I summarized the common concept of the project result:
It based on Tom’s story from the Open Group’s video series of IDM. The concept is to create a new service which contains two parts: One is a new platform to help Tom better manage his personas and identity attributes in a holistic way, the second part is to find a way to let Tom get access to the new platform securely and friend. The benefit of the service would be repetition and frustration reduction, give users more control of personal data, make online life easier and encourage users to deal with their online identities in a healthier way.
Iterative process of Discover & Define stages
This diagram shows the iterative process of my Discover & Define stages. I started from exploration through literature reading and case studies, group the information I got and make reflections through visualization methods such as mind-map, then define the research direction further through user research. After defining my research question in more detail I will go back to search for more resources.
Building identity ecosystem
NSTIC (National Strategy for Trusted Identities in Cyberspace) describes a vision of the future—”an Identity Ecosystem—where individuals, businesses, and other organizations enjoy greater trust and security as they conduct sensitive transactions online.” “Key attributes of the Identity Ecosystem include privacy, convenience, efficiency, ease-of-use, security, confidence, innovation, and choice.” Here NSTIC shares several examples of identity ecosystem, which are quite close to my project vision. Identity Ecosystem is a good concept representing my goal of the new service I want to build in this project.
Searching with keyword of “Identity Ecosystem” I find one amazing video series by The Open Group about Identity Management. They discuss concise and distinct concepts and principles of identity management through fairly vivid examples and stories with strong sketch animation style. It’s a good way to clearly explain identity management concept to people who don’t know it before. The videos are also very useful because they talk a lot about different personas and identity attributes one person has, which closely relate to multiple identities in my project. I organize the useful key concepts of how people operate their identity from the video series in one simple sketch:
Take Tom in the videos as example, he has a core identity of person who he is. In the digital world, he uses the unique core identifier to get access to different personas which are shared for different situations. For each persona there are various identity attributes of Tom and he keeps them from exposure to other parties to minimize attributes aggregation and thus to keep privacy control. The real identity attributes aggregation of Tom, which links to his core identity should be stored in a super repository that only Tom can get access to it.
To watch the video series:
Identity Management: Identity First Principles
Identity Management: Operating with Personas
Identity Management: Trust and Privacy