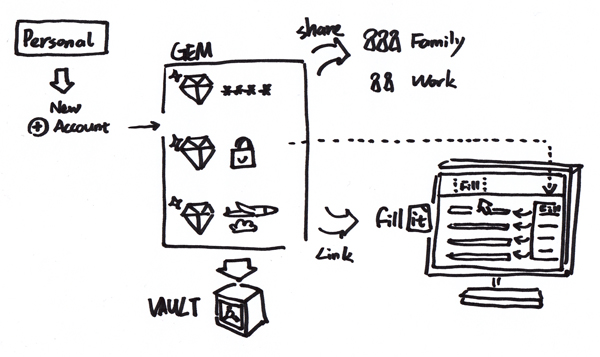
(Elements comparison table of three main password management services)
There are three main password management services nowadays-1Password, LastPass and KeePass– and their system and function is quite similar to the outcome my Master Project would like to achieve. Therefore it’s very meaningful to study on these three services. As a start I gave a trail with each of them and experienced how they work. Then I collected more online comments and tutorials from others to make a comparison within these three services. As the above table shows there are many different features within the password management services and here are the common elements:
- Master password: To get access to the management system, users need to set a master password and must remember it-the service cannot help you get back the master password any longer because it will not save the password to guarantee users’ security control;
- Password separation: As users get access to the password management service with one master password, there is no need for them to remember password for each online platform. Therefore users can set super strong passwords for each site and the service could help users generate random and strong passwords- it encourages users to set stronger but harder remember passwords;
- Browser plug-in: Most services are based on browser and work as plug-in. In this way when users login or create a new account the plug-in could help automatically generate, remember and fill in accounts information and that saves users’ lots of time;
- Devices sync: Most services support data sync across various devices and systems. It works as cloud storage or data file saved on Dropbox. However, the user experience across devices might be affected by inconsistent interfaces, prices or developers;
- Function: Most services are focusing more on password management. Some of them offer identity or account management as well but just work in the same approach of password management and that don’t fit IDM requirements quite well.